Why data protection regulations are always behind?
It is very hard for regulators to predict what new technology will emerge. Therefore, lawmakers tend to wait for an incident to happen and then decide which regulations to apply to it.
The answer lies in the nature of regulations. Of course, a perfect regulator should predict an impending issue and prevent it. The problem is that only some regulators are intelligent IT specialists. When a new technology is just emerging, regulators need help to predict harmful consequences. Therefore, it is much more reasonable for people who make laws to wait for an incident to happen and then decide which regulations should be applied to it.
Think back to the biggest data-leak scandal in Facebook history. It was reported by The Times that in 2014 contractors and employees of Cambridge Analytica acquired the private Facebook data of tens of millions of users. Stephen K. Bannon, Trump aide, misused data obtained from Facebook to build voter profiles. However, an investigation was initiated by Cambridge post factum when the massive data leak had already occurred.
For sure, the government tries to regulate website tracking by forcing to comply with GDPR, for instance. On the other hand, the market has already adapted to the recent regulations. And least likely other GDPR will take place in 2–3 years. There are so many people who commercially benefit from sharing and analyzing your data, that they will always find a way to go the law around. New technologies allow them to continue tracking and advertising, targeting people indirectly.
Cryptocurrency is an excellent example demonstrating the relationships between regulations and emergent technologies. Cryptocurrency has been around for a while, since the beginning of the 2010-s. But still, they have been investigating its mechanics and trying to regulate it.
As you see, the consequences of any incident fall on the ordinary users' shoulders, not on the regulators' ones. There are no state holders who are interested in not leaking your data. It is the user who is interested in the security and privacy of their data.
Then how to protect yourself from the risks leading to data leakage?
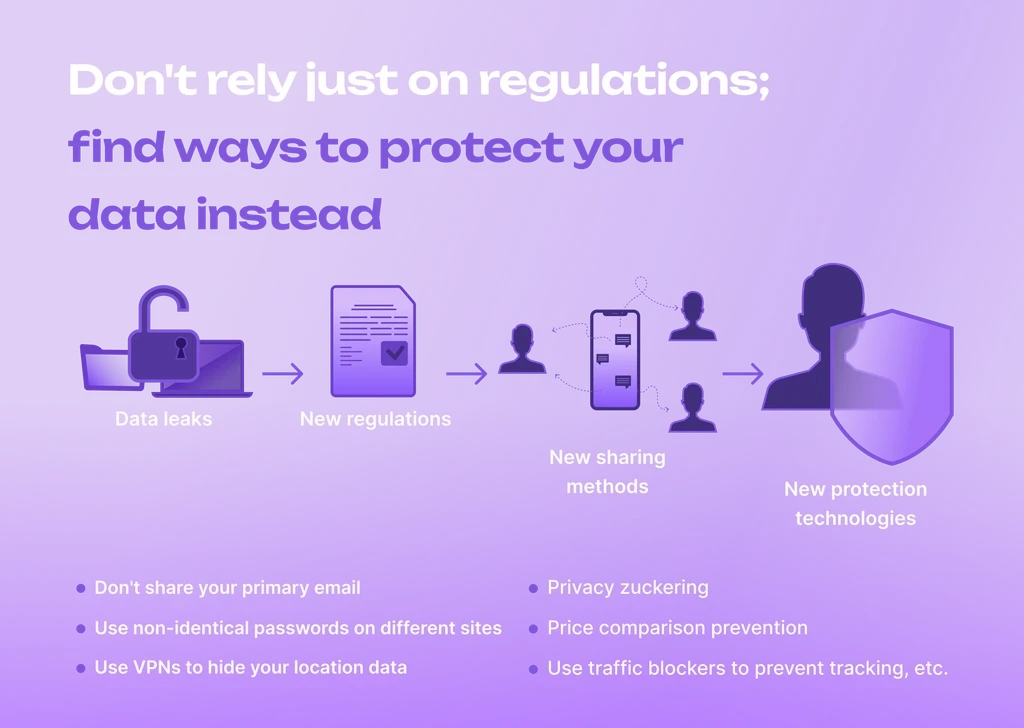
Newton's third law of motion states that every action has its equal and opposite reaction. If you want to be one step ahead, you should use the same rule. The same technology is the only tool to counteract the effect of new technology. If someone is trying to leak your data, you should be aware of how to block this, not waiting for regulations. Some tools that prevent hackers from leaking your data are:
not giving them your primary email;
using non-identical passwords on different websites;
using VPNs that don't indicate your location;
using net blockers to prevent tracking, etc. If an emergent technology poses a risk, don't rely on regulations; find ways to protect your data instead.
Subscribe to our newsletter to receive a quick overview of the latest news on human risk and the ever-changing landscape of phishing threats.