From Phishing to Spear Phishing: A Deep Dive

Cyberattacks have grown exponentially in sophistication, particularly in the realm of phishing. Phishing remains the most common form of cybercrime, with an estimated 3.4 billion phishing emails sent daily by cybercriminals, disguised to appear as legitimate messages from trusted sources. This translates to over a trillion phishing emails per year. While general phishing casts a wide net, spear phishing takes it further—targeting specific individuals or organizations with a highly tailored approach. In this article, we will explore the evolution from phishing to spear phishing, examine the risks they pose to businesses, and outline strategies to mitigate these threats.
The Phishing Trap
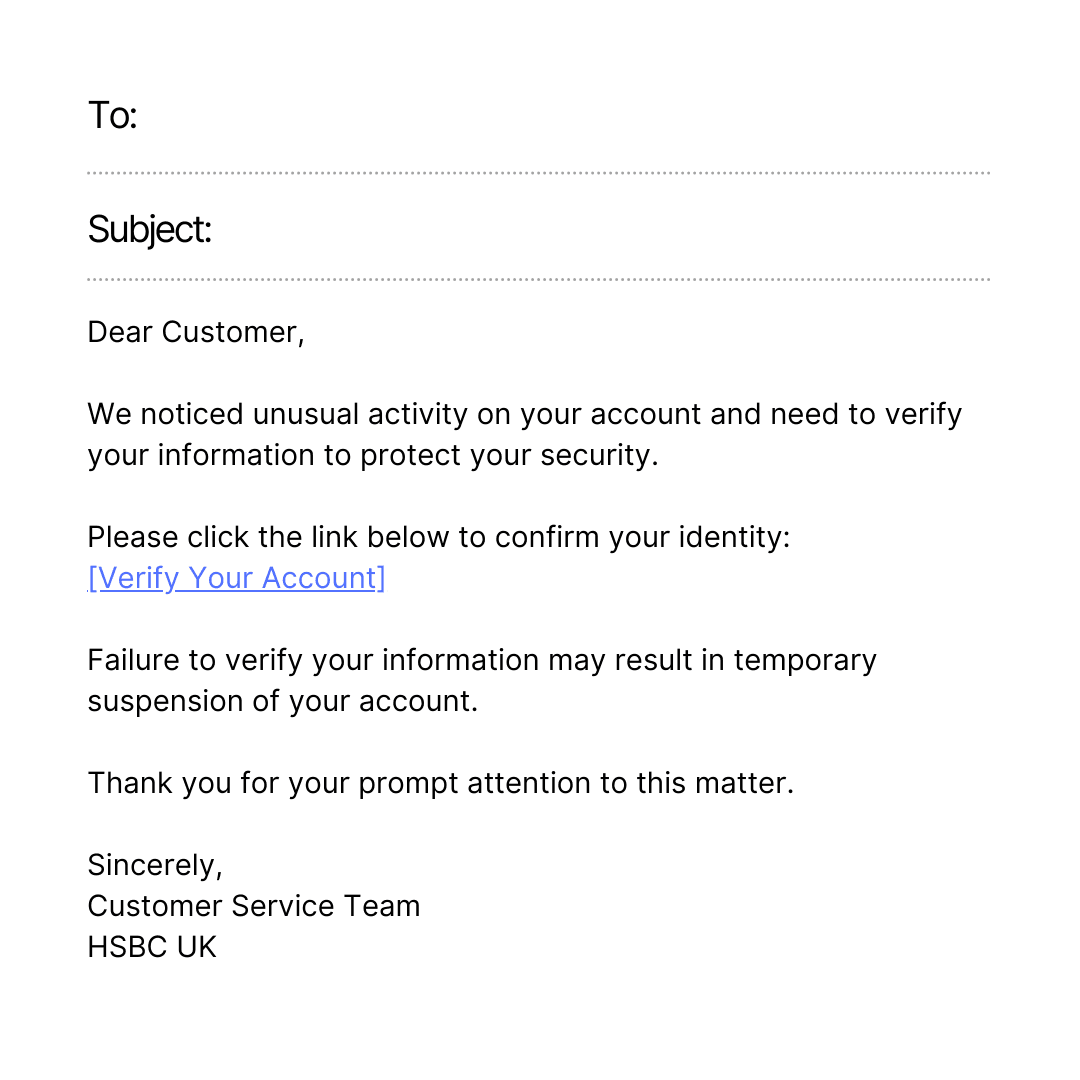
Phishing is a type of social engineering attack where cybercriminals pose as legitimate entities, usually via email, to deceive individuals into revealing sensitive information such as login credentials, credit card details, or installing malware. Common phishing emails mimic well-known companies, government organizations, or internal messages from the victim's own company.
Cybercriminals frequently employ scare tactics or urgent requests to compel recipients to act quickly, and these fraudulent communications typically lack personalization, featuring generic content. In traditional phishing, attackers send thousands of generic messages to as many potential victims as possible. The goal is quantity—casting a wide net in hopes that someone will fall for the scam.
Exploring Varied Attack Vectors
Phishing can occur in various forms, including:
Email Phishing: The most common form, where attackers send bulk emails that appear to be from legitimate organizations, tricking recipients into clicking malicious links or providing personal information.
Vishing: Phishing conducted over phone calls, including Voice over Internet Protocol (VoIP) systems.
Smishing: Phishing via text messages, or SMS phishing, which can also infect mobile devices with malware.
Wire Transfer Phishing: This variant targets bank transfers to fraudulent entities.
Clone Phishing: Attackers create an identical copy of a legitimate email previously sent to the victim but replace attachments or links with malicious ones.
In this volume-driven strategy, even a small percentage of success from thousands of attempts can lead to significant breaches.
What is Spear Phishing?
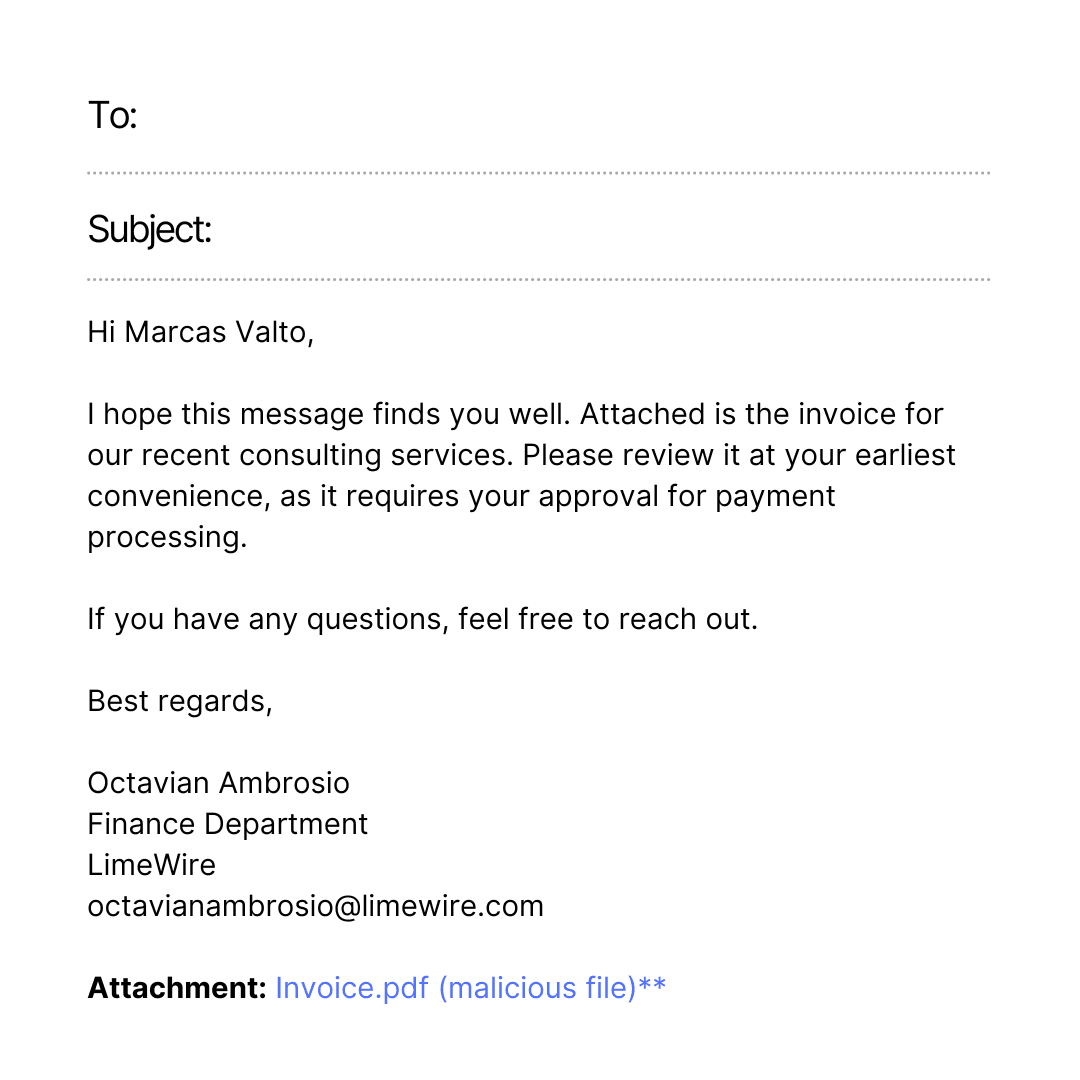
Spear phishing is a more refined version of phishing. Instead of targeting the masses, spear phishing involves cybercriminals conducting research on a specific individual or company. The attacker may study the target's online presence, social media profiles, and business relationships to craft a highly personalized and convincing message. This tailored approach often leads to much higher success rates compared to broad phishing attempts. In industries like financial services and healthcare, where personal data and financial information are top targets, the stakes are even higher.
How Spear Phishing Works
A spear phishing email may appear to come from the CEO of the company, instructing an employee to make an urgent wire transfer or approve access to sensitive documents. Since these messages exploit trust and urgency, employees are more likely to comply.
This level of personalization makes spear phishing incredibly dangerous, as even the most cautious employees may find it difficult to differentiate between a real and a fake request. In fact, although spear phishing represents only 0.1% of all email-based phishing attacks, it is responsible for a staggering 66% of all data breaches.
The Impact of AI on Spear Phishing Tactics
In traditional phishing, AI can automate large-scale campaigns, generating convincing phishing emails that evade spam filters by using natural language processing to create realistic content. However, AI's real power comes in spear phishing, where it helps cybercriminals craft highly customized messages.
In spear phishing, AI can:
Analyze data at scale (social media, professional networks, any public information) to find personal details about a target.
Generate personalized messages that mimic writing styles and organizational contexts.
Automate complex research to identify high-value targets, like executives in companies.
Deepfake impersonation (using AI-generated voice or video).
This evolution allows attackers to execute more successful spear phishing campaigns with less effort.
Types of Spear Phishing
Spear phishing comes in various forms depending on the specific goals and techniques used by attackers. Here are some of the most common types of spear phishing:
Business Email Compromise (BEC) is aimed at stealing money or sensitive data from businesses. In a BEC attack, cybercriminals impersonate trusted individuals, such as managers, coworkers, or external partners like vendors and clients.
CEO Fraud (Whaling) targets high-profile executives like CEOs or CFOs. Attackers research these individuals thoroughly.
The Dangers of Spear Phishing
For CISOs and IT security managers, spear phishing poses a unique set of challenges. Beyond the financial costs, which can amount to millions of dollars per incident, the reputational damage can be devastating—particularly in industries where trust is paramount, such as healthcare and finance.
Financial Impact
According to the Cost of a Data Breach report, the typical phishing-related breach incurs a cost of USD 4.76 million, but spear phishing incidents can reach up to USD 100 million.
Regulatory Compliance Risks
Industries that handle sensitive personal data face additional risks related to compliance with regulations like GDPR and HIPAA. A successful spear phishing attack that leads to a data breach could result in significant fines and penalties, not to mention loss of trust among clients.
For example, under the GDPR, British Airways was fined £20 million by the UK's Information Commissioner's Office (ICO) for failing to protect personal and financial data in a breach that exposed the sensitive information of over 400,000 customers. The breach, which resulted from a phishing attack, could have been prevented had stronger security measures been in place.
Building a Strong Cybersecurity Shield for Your Company
Phishing attacks are among the most challenging cyber threats to counteract, particularly because traditional cybersecurity tools often struggle to detect them. Mitigating the threat of phishing requires a multi-layered defense strategy.
Comprehensive Security Awareness Training
Human error remains one of the most significant vulnerabilities in cybersecurity. Training your employees to recognize phishing and spear phishing tactics includes educating them on spotting red flags like suspicious email addresses, unexpected requests, and grammatical errors. Regular phishing simulations can reinforce these lessons. Brightside AI can assist in automating phishing simulations and monitoring user behavior.
Strengthening Identity and Access Management (IAM)
Implementing robust IAM controls, such as role-based access and multifactor authentication (MFA), adds critical layers of protection. Even if an attacker manages to steal a user’s password, they’ll be blocked by MFA.
Advanced Cybersecurity Controls
While traditional email filters and firewalls are a start, combining them with more advanced tools provides a higher level of protection. Tools like secure email gateways, antivirus software, and endpoint detection solutions can identify and block phishing attempts before they reach the user.
Regular System Updates and Patching
Attackers often exploit known vulnerabilities, and keeping your systems current closes many potential attack paths. With Brightside AI, your organization can automate the patching process. Our AI-driven technology scans for vulnerabilities across your network and ensures patches are applied promptly, reducing exposure to potential threats.
Monitoring with AI-Powered Solutions
Monitoring network activity with Brightside AI allows for real-time detection of unusual behaviors that may indicate an active phishing attack.
Incident Response Planning
Having a well-defined incident response plan in place allows organizations to act quickly in the event of a spear phishing attack. This includes containment, communication protocols, and a clear path to recovery, ensuring minimal downtime and damage.
Bottom Line
Understanding the nature of phishing attacks—from the broad strokes of traditional phishing to the targeted precision of spear phishing—is crucial for any business. A strong defense includes a combination of employee training, advanced security tools, and a proactive approach to cyber hygiene. By implementing these strategies, along with the power of Brightside AI, your organization will stay one step ahead of attackers, with intelligent defenses that adapt to emerging threats.
Subscribe to our newsletter to receive a quick overview of the latest news on human risk and the ever-changing landscape of phishing threats.